With the recent attacks of WannaCry and NotPeyta, SMB1 has been shown to have the security features of a chocolate fire guard. NetBIOS Name resolution is the equivelant of shouting for Bob in a room of people and accepting the first person who replies “Yes thats me!” Given we are putting together a nice secure environment, we really don’t want these in use. If you remember when we provisioned our domain controllers, we removed SMB1 from them. Are you going to remember to do this on all your devices? What about when you’re addressing this from an established domain? Lets now use Group Policy to kill these with fire.
SMB1
Although we removed SMB1, to make sure it’s disabled we will configure the registry using Group Policy Preferences. We will use the Custom Default Domain Policy we created earlier to do this as we want it disabled globally.
Disable SMB1 Server
Create a new preference under Computer Configuration\Preferences\Windows Settings\Registry
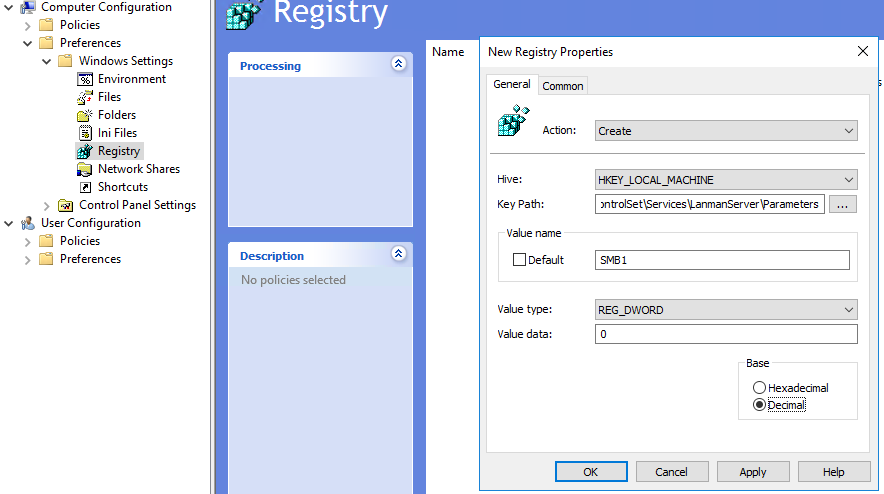

Create a registry entry with the following settings:
- Action: Create
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
- Value name: SMB1
- Value type: REG_DWORD
- Value data: 0
Disable SMB1 Client
This uses two registry entries, one to disable SMB1 and then 1 to configure the Lanman Workstation service to no longer require it.
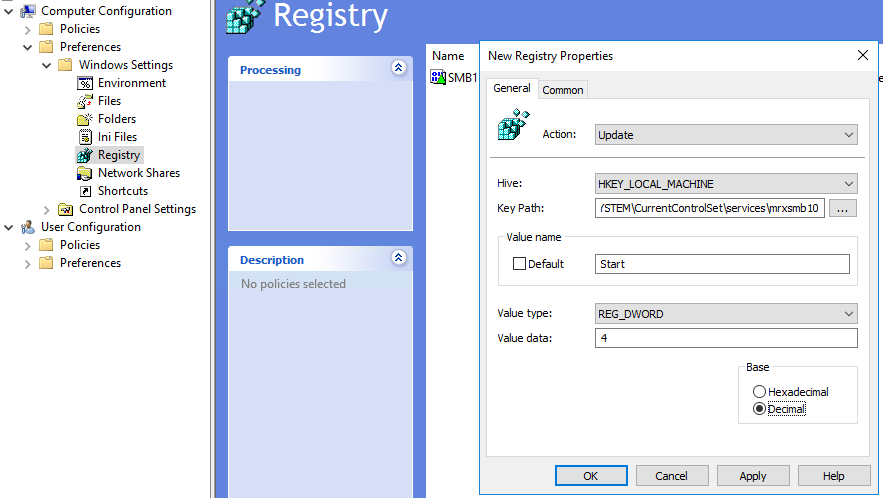
- Action: Update
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SYSTEM\CurrentControlSet\services\mrxsmb10
- Value name: Start
- Value type: REG_DWORD
- Value data: 4
And finally configure the service
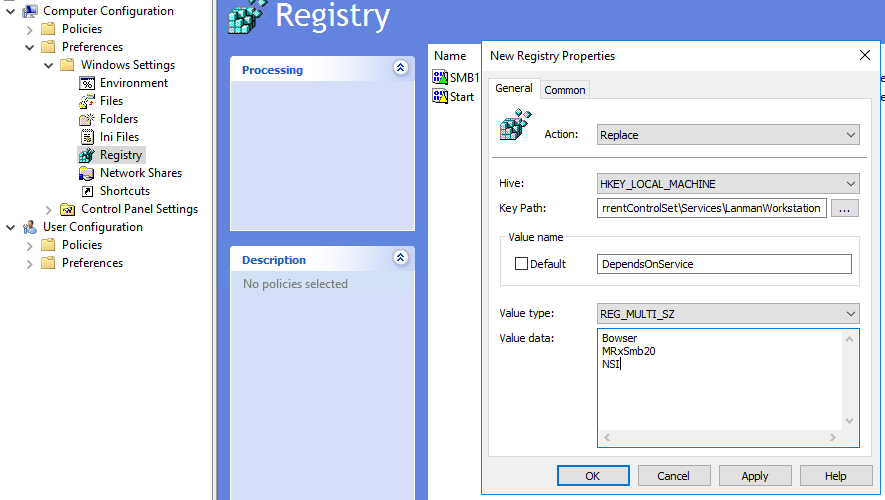
- Action: Replace
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SYSTEM\CurrentControlSet\Services\LanmanWorkstation
- Value name: DependOnService
- Value type REG_MULTI_SZ
- Value data:
- Bowser
- MRxSmb20
- NSI
Do a GPUpdate and reboot and you should no longer have any SMB1 in use in the case you haven’t removed it or are using some Windows 7 devices.
REF: https://blogs.technet.microsoft.com/staysafe/2017/05/17/disable-smb-v1-in-managed-environments-with-ad-group-policy/
NetBIOS
NetBIOS has a two-prong attack for disabling it. We use GPO to set the client to only ever use a WINS server (which we havent deployed so effectively disabling NetBIOS). We also configure DHCP options to disable it for machines that aren’t necessarily joined to the domain (think autoscale services, Build Servers etc).
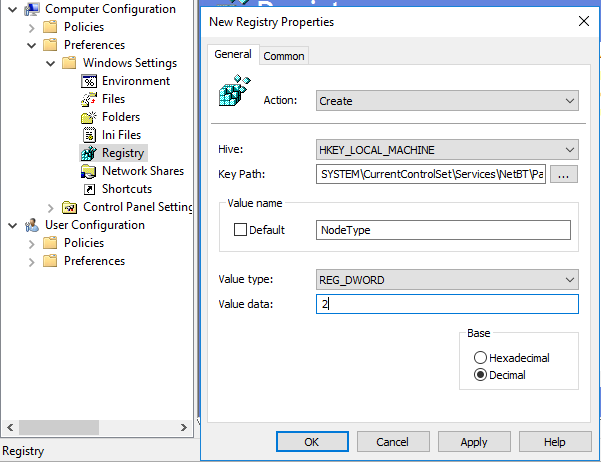
First of all, lets use GPO to configure the name resolution to use WINS only. We will do this on a global level again by editing our custom default domain policy. In the same way that we disabled SMB1 above, we will use group policy preferences to create the following registry key:
- Action: Create
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SYSTEM\CurrentControlSet\Services\NetBT\Parameters
- Value name: NodeType
- Value type REG_DWORD
- Value data: 2
Last step, we will configure the DHCP option to disable NetBIOS name resolution. To do this we need to open the DHCP management console and for each DHCP server on your network configure the following DHCP option under your server options so that it applies to all scopes:
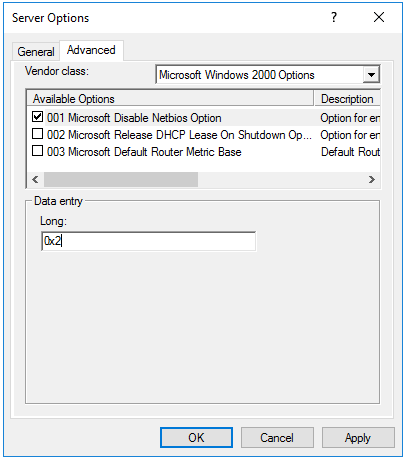
The option to set is found in the advanced tab and then select Microsoft Windows 2000 Options. Place a tick next to 001 Miucrosoft Disable Netbios Ooption and set the value to 0x2.
You can use either Wireshark or Microsoft Message Analyzer to inspect your network traffic and ensure that NetBIOS and SMBv1 are no longer in use.

thank you!