The first thing we will tackle are the issues raised by the Microsoft Best Practice Analyser. A lot of these issues are more generic to Windows devices so what we will do is create a new “Default Domain Policy” which will apply throughout. Start by opening the Group Policy Management Console, on the left navigate to the Group Policy Objects container. Right click the container and select New. Give it a name for example, Custom Domain Policy and click OK. This will go through and create a new blank GPO that we can build upon.
The first thing we will do, is force the advanced auditing that we setup earlier. We will replicate this auditing to the member servers and workstations so in our main domain policy we will enable it.
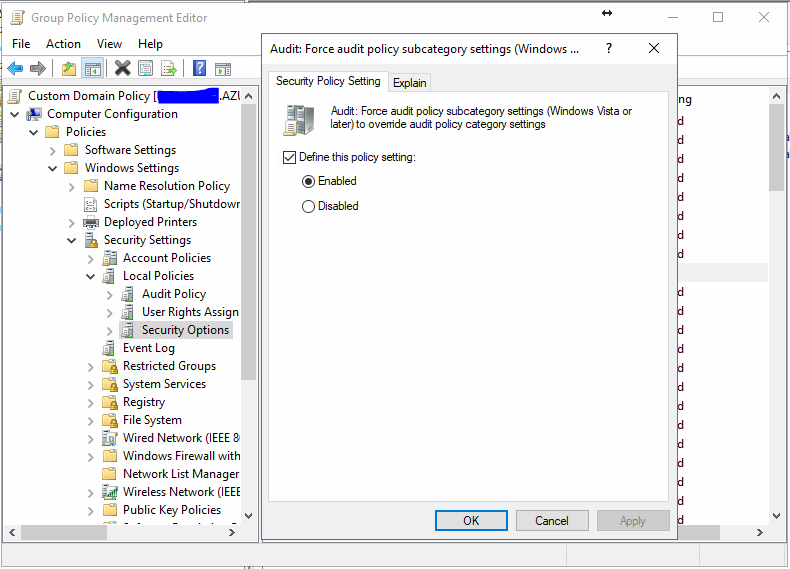
With this setting enabled, click apply and OK. Next we will disable anonymous enumeration of shares and accounts. If you plan to use a 1-way trust further down the line, this will cause problems. If you’re not planning to do a 1 way trust, enabling this will be fine.
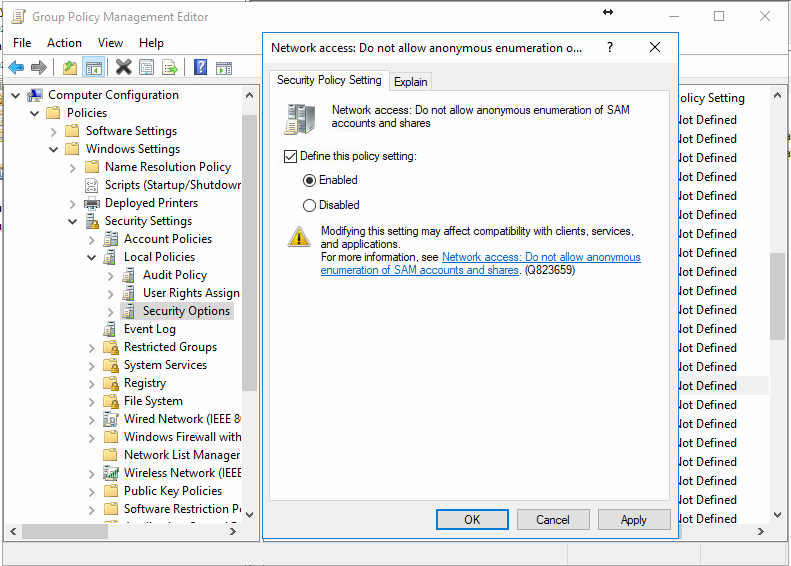
Again, apply and OK to exit the editor. Whilst we are in the Security Options window, we will force signing of all SMB communications. Unless you are planning to deploy old, out of date systems in your environment you should have no issues enabling these options
- Microsoft Network Client: Digitally Sign Communications (Always)
- Microsoft Network Server: Digitally Sign Communications (Always)
- Microsoft Network Client: Digitally Sign Communications (If Server Agrees)
- Microsoft Network Server: Digitally Sign Communications (If Client Agrees)
With these settings enabled, close down the Group Policy Management Editor window, which will save the GPO. Go to the root of your domain where the Default Domain Policy is linked, right click and select Link Existing GPO. Now, you can link the Custom Domain Poliy we have just created.
The last part of this initial hardening process we need to complete is to remove the ability for Server Operators to remotely shut down domain controllers. We will restrict this right for our Administrators only. Again, rather than edit the default domain controllers policy, we will create a custom policy that we will later link to the Domain Controllers OU. If you wish, you can re-use the audit policy we created earlier and name it appropriately.
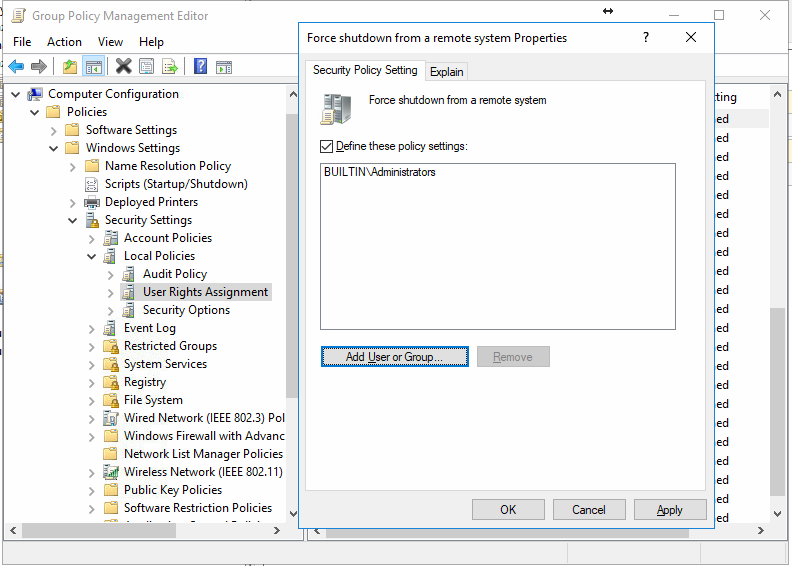
Once configured, Apply, OK, close Group Policy Management Editor and then link the new (or reused) GPO to the domain controllers OU. Ensure that the GPO has a link order of 1 to ensure that it overrides the Default Domain Controllers policy which has Server Operators with the permission to shut down the server. To do this, navigate to the Domain Controllers OU in the Group Policy Management Console, and highlight the new Custom Default Domain Controllers policy. Click the double up arrows to move it to the top and that should be it.
With all of these in place, the Critical issues that are raised by Microsoft OMS should disappear. There is still a long way to go with securing the Active Directory environment however this is a start, a small start. Once again I have put these custom policies within my GitHub repository so that you can import them.
