As discussed in Adding Exchange to the Lab, I wanted to create a DMZ based Transport Server, just to complicate things, and why not. So to start with, I have done a Windows Server 2019 Core VM in the DMZ network. This has been named, AVMA key installed, fully updated (2020-11 update). The ISO has been mounted and ready to go.
We start with the pre-requisites, there are fewer of these for the Transport Server role, just DotNet framework, Visual C++ 2012 and the Active Directory Lightweight Directory Service! I won’t go through the installation of the software as it’s similar to the mailbox server role.
As this is not a domain joined computer, you need to manually set up the FQDN before Exchange will install. A good article on how to do this for Server Core can be found at Jaap Wesselius’ blog. I ended up using PowerShell to do the following
Set-ItemProperty -Path HKLM:\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters -Name 'NV Domain' -Value lab.marklewis.blogSo, lets go through the installation and run setup.exe
No updates were found, so happy days, click Next. At this point it copies the files required.
Accept the license terms
I am going to use the recommended settings here
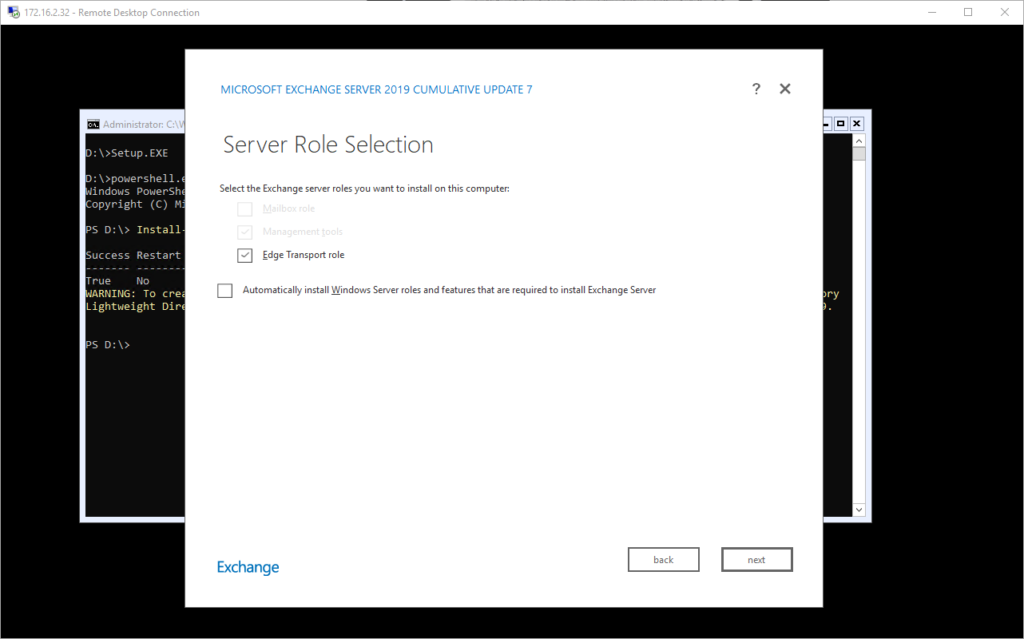
Then, we select just the Edge Transport Role, you’ll notice I’ve already installed the ADLDS feature in the background so no need to tick the box here.
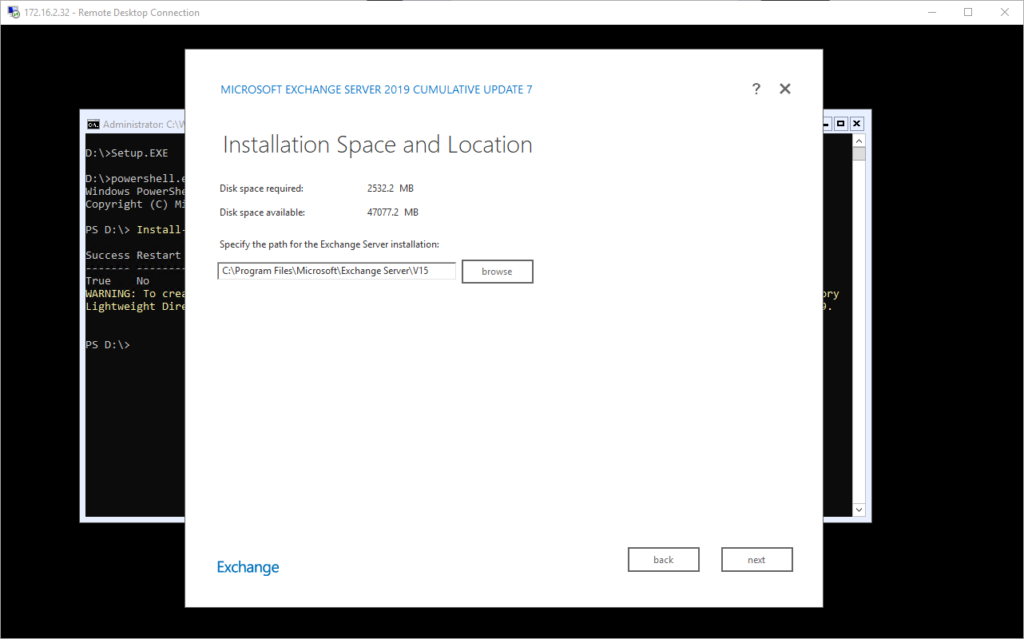
Next, we specify where to install it
It will verify the prerequisites are done when you can then click install
And wait …..
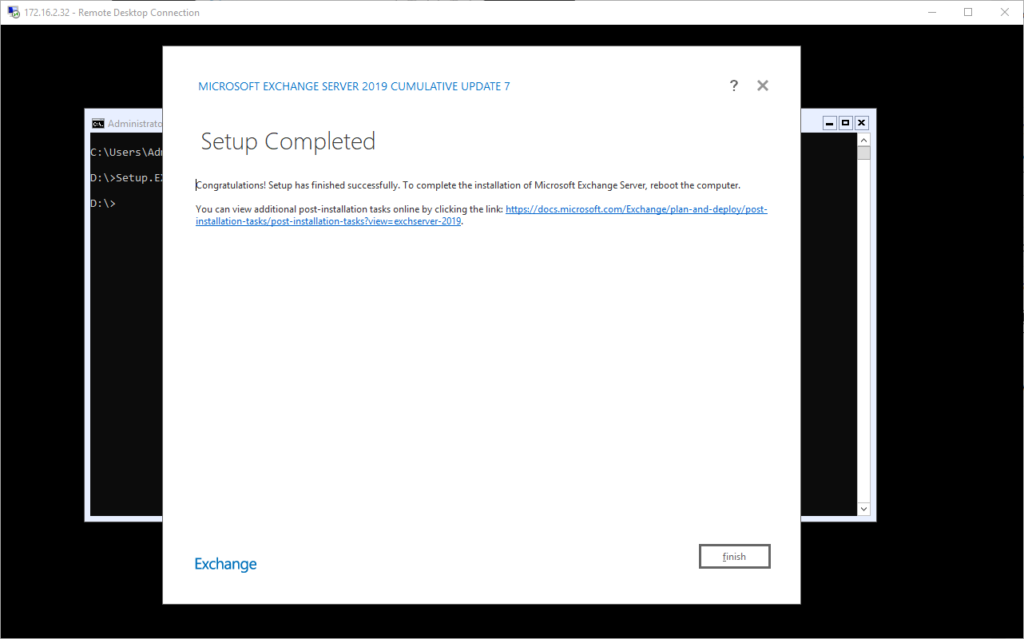
I will admit I have no idea how long this took, if it was as long as a mailbox server as I just set it off and went to do other things. As requested, I rebooted the server and then began to work on the post installation set up.
First thing that I needed to do was ensure that names were resolvable between the Transport Server and Mailbox Server. I edited the hosts file on the transport server due to lack of a DNS server (DNS is forwarded on via the router).
Next, I made sure I had added the domain (marklewis.blog) to the Exchange server as an authoritative domain. I configured the address policy that I wanted to use. To access the management console on the transport server, I opened PowerShell then ran
exshell.psc1Followed by
exchange.ps1At this point, I was able to create a new subscription using he following PowerShell
New-EdgeSubscription -FileName C:\tmp\EdgeSubscriptionInfo.xml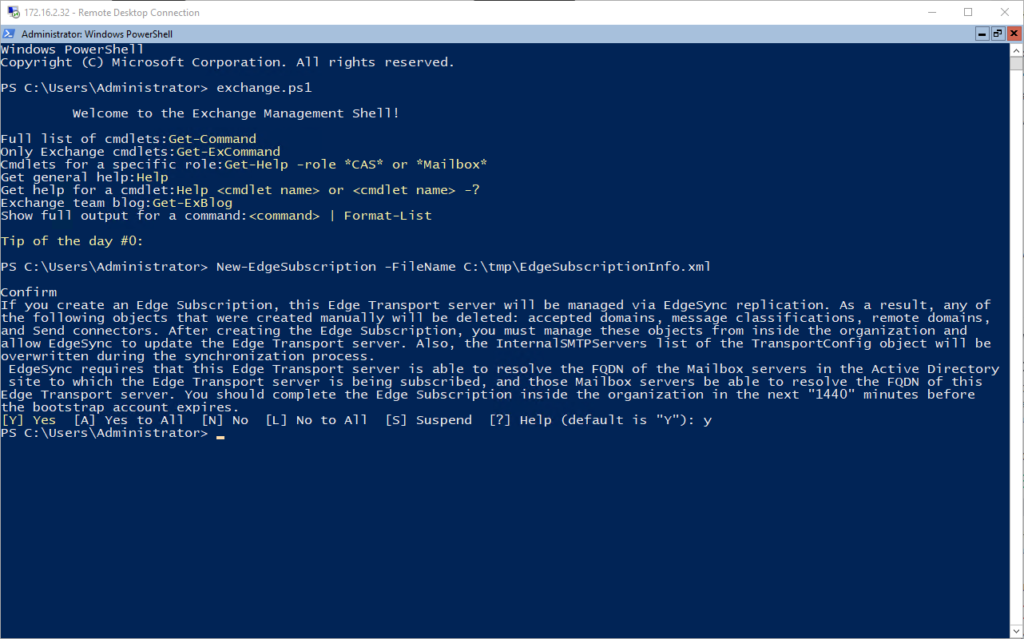
Now we have the file, we need to copy it to the mailbox server. At the moment, my firewall rule between the DMZ and LAN allows for full access between the Transport Server and Mailbox Server. I mapped a drive, copied the file over then jumped on to the Mailbox Server. Running
LaunchEMSfrom a command line fires up the Exchange Management Console. Then running the New-EdgeSubscription cmdlet. I had to specify the AD Site where my Exchange Mailbox Server is as a source for the syncronization process.
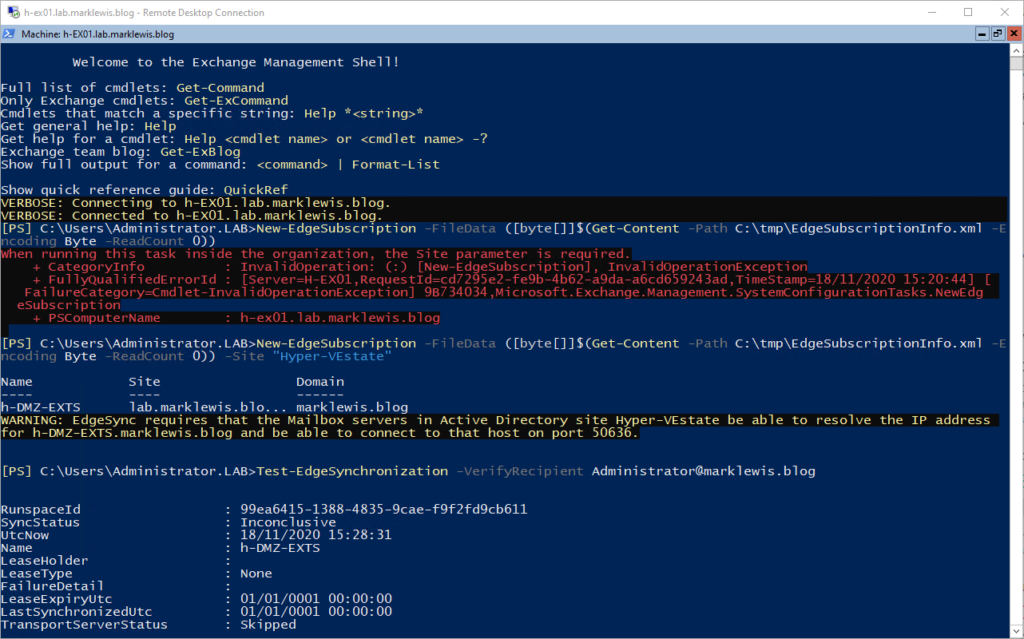
I waited about 15 minutes and then tried sending a test mail:
Received: from h-EX01.lab.marklewis.blog (192.168.20.8) by h-DMZ-EXTS.marklewis.blog (172.16.2.32) with Microsoft SMTP Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id 15.2.721.2; Wed, 18 Nov 2020 +0000 Received: from h-EX01.lab.marklewis.blog (192.168.20.8) by h-EX01.lab.marklewis.blog (192.168.20.8) with Microsoft SMTP Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id 15.2.721.2; Wed, 18 Nov 2020 +0000 Received: from h-EX01.lab.marklewis.blog ([fe80::30ad:484c:7638:3440]) by h-EX01.lab.marklewis.blog ([fe80::30ad:484c:7638:3440%5]) with mapi id 15.02.0721.002; Wed, 18 Nov 2020 +0000
Looking at the headers, that worked! Next, I need to update the firewall rules to allow SMTP(S) traffic and then set the MX record and SPF Record. Before this though, I created the shared mailbox, like I currently use, ready for the occasional mail to come through.
With the public DNS records updated, mailflow was working back and forth. Lastly, I will add the product key, using the Exchange Management Shell.
Exchange Server doesn’t have a built in DKIM mechanism, something I did make use of on Office 365.
I was asked on Twitter if I covered the ACLs before and after installation of Exchange in Active Directory, this is something I will attempt to do an in depth look at what it does.
