One of the common mistakes that people make is to use GPO (No longer an option)/Scripts/Build Processes to standardize the local administrator account password. Whilst this can be great for convenience, an attacker will use this to move laterally throughout your network. To stop this, we use the Microsoft LAPS (Local Administrator Password Solution). It’s a free download from Microsoft directly. Currently using v6.2. It’s a nice quick, easy win to improve security on your directory environment.
What is LAPS?
LAPS has three main components to it. There are two Active Directory attributes that need adding to the Schema, you have the client Group Policy Extension which needs to be installed on all your workstations. The last part are the administrative tools (LAPSUI, ADMX files and PowerShell cmdlets) which you install on your administrative workstations. LAPS is configured by GPO for frequency of change, length, complexity etc. Deploy LAPS to your workstations and servers but NOT your domain controllers.
Deploying LAPS
Microsoft provide as part of the main LAPS download some very comprehensive documentation on how to deploy LAPS. As well as deploying the software and configuring it, when you are deploying in your environment you will need to educate your teams to ensure they are aware of how to retrieve a password. This shouldn’t be common place use of course as you should be using a dedicated audited workstation admin account.
Before we start deploying LAPS, we will do some prep work that will be used later on. The first thing to do is create the groups you will use to restrict and audit the retrieval of passwords. This will come down to exactly how you wish to secure your environment, your levels of permissions and levels of staff. A minimum of 1 group is required if you wish for anyone using LAPS to view passwords regardless of if its a server or workstation. Maybe you only want support staff in a location to access passwords of workstations in that location. This is a decision that you must make depending on your environment.
The first part of deploying LAPS is to install the LAPS client and tools on your administrative workstation. Installing the tools gives you PowerShell commands which are then used to extend the schema and configure the permissions. This installation is a simple MSI, next next next making sure you select the full suite of tools when given the option.
With the tools installed, the first job is to extend the schema. To do this, your administrative account must be in the Schema Admins group. Once you’re in the Schema Admins group, you will need to logoff and back on for it to take effect. After logging back on, open PowerShell and begin extending the Schema:
Import-module AdmPwd
Update-AdmPwdADSchema
Next job is to enable the machines to write their passwords:
Set-AdmPwdComputerSelfPermission -OrgUnit "OU=MyComputers,DC=contoso,DC=com"
The next step is to grant access to the group(s) we created earlier to read and reset the passwords:
Set-AdmPwdReadPasswordPermission -OrgUnit "OU=MyComputers,DC=contoso,DC=com" -AllowedPrincipals "<<Security Group>>"
Set-AdmPwdResetPasswordPermission -OrgUnit "OU=MyComputers,DC=contoso,DC=com" -AllowedPrincipals "<<Security Group>>"
With the schema extended and the permissions set, it’s time to deploy the LAPS client to your workstations. You have multiple options for this which is outside of the scope of this post but options include GPO MSI push, PowerShell/batch script, manual install or SCCM.
Now we are ready to start configuring LAPS. Configuration is done via GPO. Add the ADMX file from your workstation to your GPO Central Store (Group Policy – Central Store) so that any admin workstation can edit it if required. Once the central store is updated and replicated, either edit your default workstation GPO (NOT the Default Domain Policies) to configure your desired options (password complexity, which account and enable LAPS).
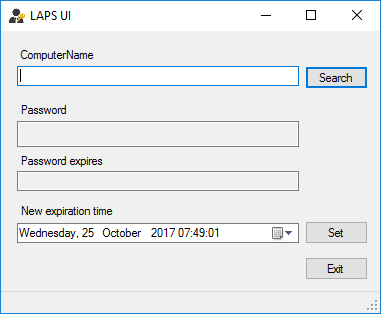
Now, should you require the admin password you can either use LAPSUI:
or PowerShell:
Import-Module AdmPwd.PS
Get-AdmPwdPassword <<ComputerName>>
Test in your environment and STOP using the same local admin password today!
